Ping SMS Spam. Secret Weapon of Phishers and Brokers.

Ping spammers, AKA active number spammers, are the ever-present phone trolls flooding your inbox with SMS messages, trying anything and everything to get you to respond. They want you to verify that your phone number is active.
Verification that your phone number is active is the first and primary goal of the Ping Spammer.
Pro tip: Don’t engage!
Subscribe to get new insight every week you won't find elsewhere. We are not here to cover news or market services to you. Our only goal is to share insights we find as we research and operationalize the recovery of privacy for our clients.

The Goal of Ping Spammers
Ping spammers build and maintain lists of active phone numbers to sell. They want you to respond to confirm your phone is active.
The lists they build are often passed on to other spammers or scammers for targeted campaigns. And sometimes, they’re sold to data brokers who profit from your engagement.

The Tactics of Ping Spammers
These spammers often disguise their messages to appear as legitimate, like a delivery notification or a missed call alert.
They may also send generic messages or vague questions designed to pique your curiosity, such as random questions from an unknown sender.
- "Lost my phone! Who is this?"
- "Are you still coming to dinner tonight?"
- "Have you talked to Kevin lately? I'm worried."
- "Hey! It's been a while. How have you been?"
- "Don't forget the party this weekend! Let me know if you're coming."
Ping spammers are impersonating political ads, hoping you’ll click through or respond with a "STOP." For instance, Jeff recently received a series of political ads from a ‘campaign,’ each coming from a different phone number.

What Happens If I Respond?
At a minimum: more spam. While ping spammers might not always have immediate malicious intent, their actions significantly contribute to the broader issue of spam and unwanted communication.
By validating your phone number, they enable other malicious actors to target you with more spam and potentially more severe scams. Some ping spammers might even engage with you directly if you respond.

How Bad Can It Be?
Interacting with a Ping Spammer gives up more information than people realize. Just responding is bad. Interacting tells them a lot more, including that you are naïve about how the internet works. With the tools available today, it's easy to find you, and then scam you - or steal your identity.
This episode of the Fraud Squad walks you through exactly how:
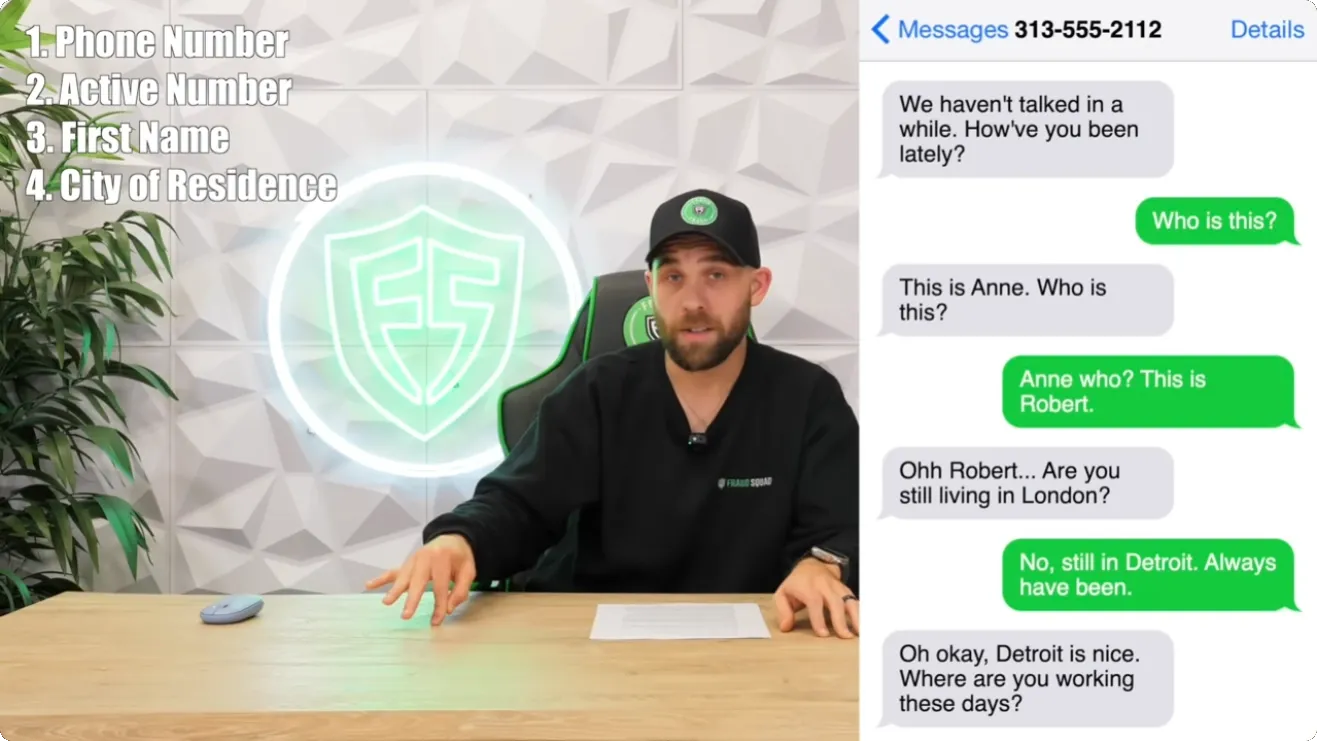

Who is Responsible?
Evidence suggests that data brokers, including lead generation companies and people search engines, are connected to ping spammers. While scammers are always after your data, brokering is a lucrative business without needing to resort to outright crime.
Lead generation companies and people search engines collect vast amounts of personal data, and active phone numbers are critical identifiers in these profiles. Ping spamming helps them verify these numbers, making the data they sell more valuable.
The only ways we know of to get verified phone numbers:
- buying from Telco's
- buying from ping spammers
- calling each and every phone…
Tactics Related to Ping Spam
Ping spam is just one method used to exploit active phone numbers. To give you a broader view of the tactics used by spammers and fraudsters, here are some related methods you should be aware of:
- Wangiri Fraud: Telecom fraud where scammers place short calls or send SMS messages to trick the recipient into calling back. Typically associated with phone calls, it's relevant when discussing tactics to confirm phone number activity. They use the return the call to charge high fees or simply validate your number.
- Smishing: Short for "SMS phishing," this tactic involves sending deceptive messages, often disguised as legitimate communication (e.g., from your bank or a service provider), to trick you into divulging personal information. Ping Spam focuses more on validating your phone number, but the line between smishing and Ping Spam can blur, as both aim to exploit your engagement.
- Gray Routing: This is the sending of SMS messages through unauthorized or cheaper channels to avoid costs and detection. Spammers and scammers use gray routes to get their messages to you without going through proper, regulated telecom channels. It makes it harder for carriers to filter out suspicious messages.
- SIM Hijacking: Also known as SIM swapping, this tactic involves fraudsters taking control of your phone number by transferring it to a new SIM card. This allows them access to two-factor auth codes - and potentially your online accounts. Once your number is verified as active, you become a potential target for more serious attacks like SIM hijacking.
- Spoofing: In spoofing, spammers use fake or misleading phone numbers to disguise the true origin of their messages or calls. This tactic makes it difficult to identify the sender. Spammers often use this method in political ad spam, sending messages from various numbers to get past traditional spam filters.


Don't Get Fooled
- Never respond: Don’t respond to unknown SMS messages. It confirms your number is active and could lead to more spam, scams, or even attempts to track you via message notifications.
- Beware the STOP: Don’t send STOP to political ad campaigns, unless you are very sure it’s actually from a campaign.
- Fake political messages: SMS STOP messages are designed to stop the spam, but if the message is fake, you just confirmed your number is active. Be careful. If you don't know for sure where that message came from, block the number instead of sending STOP.
- Report & Block: You can help filter by reporting spam/phish, just don’t respond accidently. Detailed instructions here.
- Use strong SMS filtering: The effectiveness of SMS filtering primarily depends on your telecom carrier. However, your app ecosystem, SMS app, and any third-party tools you use can also influence which messages reach you.

Avoid Quick Fix Apps
Some apps claim to fix your unwanted call and SMS spam. If those apps are collecting your personal information, accessing your messages, and accessing your contacts, just run away. They want to harvest your data, not help you.
- Avoid Apps like: 🤢🤬 Hiya, RoboKiller, Mr. Number, Sync.ME, Truecaller, Whoscall. These are call management, call-blocking, and/or caller identification apps that should be there to help you.... But instead many of them are sucking up your data, your contacts and selling you out.

Carrier Analysis
- T-Mobile: 🔥 Generally praised for its proactive approach, T-Mobile strikes a balance by filtering spam effectively without over-blocking legitimate messages.
- Verizon: 😎 Strong in spam filtering, though its aggressive approach may sometimes block more legitimate messages than users might like.
- AT&T: 😐 Effective overall, but AT&T may block more legitimate messages compared to competitors, which can be inconvenient for users.
- Smaller carriers / MVNOs: 😟 Often lacking in sophisticated filtering systems, smaller carriers may either let more spam through or flag too many false positives.
- Google Fi: 🤖 Generally strong spam filtering thanks to its use of T-Mobile's network, but performance can vary depending on whether the phone is using cellular or Wi-Fi calling. Network switching can impact consistency.
While we wouldn’t recommend changing carriers solely for spam filtering, consider tweaking spam filter settings with your provider or exploring third-party filtering tools for added control.

Which SMS App Should I Use?
- Apple: 👍 We recommend
- Apple: Apple’s iMessage
- Android: 👍 We recommend
- Google Messages
- SMS Organizer by Microsoft
Third-party SMS apps can be dangerous. Stick to apps from the major platforms.

Third Party Tools
- Apple: 👍 We recommend
- Junkman: A.I. SMS Spam Blocker (set and forget)
- SpamHound SMS Spam Filter (tinker and customize)
- Android: Unfortunately, we currently can’t recommend any specific apps. The apps that might be effective filters may also be collecting and selling your data to brokers.

Ping spammers and data brokers are becoming increasingly sophisticated, making it more important than ever to protect your digital footprint.
The best defense is awareness—knowing how ping spammers operate can help you avoid engaging and exposing your active number.
Don't underestimate the impact of a simple response. By replying to these messages, even with a "STOP," you may inadvertently confirm your number's validity, putting you at greater risk.
Filtering and blocking tools are your first line of defense. However, be cautious of apps that claim to stop spam but instead harvest your personal data. Stick to trusted carriers and SMS apps with strong filtering capabilities.
For those seeking an extra layer of protection, ObscureIQ offers advanced privacy solutions designed to minimize your exposure to data brokers. Reach out to learn more about how we can help you safeguard your privacy.
Subscribe for weekly insights you won't find elsewhere. Not news. Not marketing. Just the juicy stuff we find as we research and operationalize the recovery of privacy for our clients.
What else are we thinking about? LLM's.
Large Language Models make wide dissemination of your personal data even riskier.

Member discussion