🔥 The Ultimate Guide to an Untrackable Phone

Buying or building a privacy-focused anonymous phone
🔴 Why Every Phone is a Tracking Device
We trust our smartphones. We rely on them. But what if the very device we hold so dear is also a sophisticated surveillance tool disguised as a convenience device?
From the moment you power it on, your phone is:
- actively sharing your location by pinging cell towers (EFF.org),
- transmitting unique identifiers and leaking metadata through the apps you use and the websites you visit (The Verge).
This data, combined with your payment history, online accounts, and even your usage patterns, creates a comprehensive profile that can be linked directly back to you.
The myth of the untraceable "burner phone" is just that – a myth. Incorrect usage can expose even these devices. It's time to understand the true cost of our connected world.

🔴 Who This Guide is For & How to Use It
This guide is designed for building a fully anonymous phone—not just improving privacy. Skipping steps will compromise your anonymity.
- If you want a truly untrackable phone, you must follow every step in order.
- If you just want better privacy but don’t need full anonymity, choose a privacy-focused phone from the Grading Matrix instead.
- If you're unsure what will get you caught, refer to Common OPSEC Fails before proceeding.
Resources Below
- How People Get Caught: Real-world examples of OPSEC fails.
- Top Ten OPSEC Fails: A list of the most frequent mistakes that compromise anonymity.
- How to Stay Untracked: Understanding what it takes.
- Privacy Phone Options: Choose from pre-configured privacy phones.
- Phone Recommendations by User Type
- Going Full Tinfoil Hat: How to Build an Anonymous Phone

🔴 How People Get Caught: The Real-World
- Using Phones to Communicate on the Battlefield: When Russian forces used cell phones to communicate during the invasion of Ukraine, Ukrainian forces were able to triangulate their positions. -Army.mil
- The Dread Pirate Roberts: In 2011, a user with the handle “altoid” posted on a bitcoin forum about a new hidden service that would be an “anonymous amazon.com,” linking to a site at silkroad420.wordpress.com. Months later, the same user posted looking to hire an “IT pro in the bitcoin community,” and urged candidates to write to rossulbricht@gmail.com. That Gmail address was in turn connected to a Google+ account that posted content about Austrian economic theory, a set of libertarian ideas that was also the subject of posts on Silk Road from the Dread Pirate Roberts. -CSOnline.com
- Activist's Use of a Burner Phone as Evidence of Criminal Intent: In 2024, during the trial of activist Ayla King in Fulton County, Georgia, the prosecution argued that her possession of a "burner" phone could be admissible as evidence of criminal intent. This case highlights how merely possessing a burner phone, without proper OPSEC, can raise suspicions and be used against an individual in legal proceedings. -NLG.org
- How a series of OPSEC failures led US authorities to the alleged developer of the Redline password-stealing malware -TechCrunch.com
- Styx Stealer Creator's OPSEC Fail Leaks Client List and Profit Details -TheHackerNews.com

Most people fail OPSEC because they focus on the device and ignore their behavior. This guide fixes that.

🔴 Top 10 OPSEC Fails: Stay Anonymous
Avoid these mistakes, or your "anonymous" phone won’t stay anonymous for long. Even if you follow all the setup steps, just one slip-up can link the phone back to you.
_________________________________
1️⃣ Buying the Phone or SIM With a Credit Card or Near Home
- Why it’s a fail: Your bank transaction creates a record linking you to the purchase.
- How to do it right: Buy with cash at a store where you don’t normally shop.
_________________________________
2️⃣ Activating the Phone on Your Personal Wi-Fi or Near Your Normal Devices
- Why it’s a fail: Your home or work Wi-Fi logs the device, and cell tower data can link it to your daily habits.
- How to do it right: Activate it on public Wi-Fi at a location you never visit.
_________________________________
3️⃣ Reusing Old Accounts, Emails, or Contacts
- Why it’s a fail: Any login to an old email, social media, or contact list immediately links the phone to your real identity.
- How to do it right: Use new, never-before-used accounts and keep them separate from your real identity.
_________________________________
4️⃣ Leaving Bluetooth, GPS, or Other Tracking Features On
- Why it’s a fail: Bluetooth logs can be tracked, and GPS metadata is stored in many apps.
- How to do it right: Turn off Bluetooth, GPS, and location tracking immediately after setup.
_________________________________
5️⃣ Using the Same Routines or Locations Repeatedly
- Why it’s a fail: Even without GPS, cell towers log your movement patterns, making it easy to identify you over time.
- How to do it right: Change where and how you use the phone - never use it near home, work, or places you frequent.
_________________________________
6️⃣ Calling or Messaging Known Contacts
- Why it’s a fail: Your metadata - who you contact and how often - is just as valuable as the content of your calls.
- How to do it right: Never call or text people you already know. Use encrypted messaging apps like Session or Signal with new contacts only.
_________________________________
7️⃣ Logging Into Personal Apps or Accounts
- Why it’s a fail: Apps like Gmail, Facebook, and banking apps instantly leak identifying data.
- How to do it right: Never log into any personal accounts from your anonymous phone.
_________________________________
8️⃣ Connecting to the Same Wi-Fi or Cell Towers as Your Normal Phone
- Why it’s a fail: Even if you’re using a different SIM, your location history can link both devices.
- How to do it right: Only use the anonymous phone in different locations than your main phone.
_________________________________
9️⃣ Keeping the SIM Card or Device Too Long
- Why it’s a fail: Even if you use perfect OPSEC, long-term use allows tracking through behavioral patterns.
- How to do it right: Treat phones as disposable. Swap SIMs and devices periodically.
_________________________________
🔟 Charging the Phone at Home or in Your Car
- Why it’s a fail: Smart chargers (Tesla, EV stations, home networks) log device IDs when plugged in.
- How to do it right: Only charge using portable battery packs or in public places.
Anonymity is a discipline, not a product. Even the best phone won’t save you if you fail OPSEC.

🔴 The Challenge: How to Stay Untracked
To remain truly invisible while using telecom devices, you must master two key principles:
- Privacy: Preventing your device from leaking identifying data—especially telemetry like location, device fingerprints, and background connections.
- Anonymity: Preventing your device or accounts from being tied to you specifically. When account creation is unavoidable, you must create and maintain a false identity to prevent being tracked.
Achieving both Privacy and Anonymity is difficult. It requires:
- The Right Hardware – Not all phones are capable of being secured properly.
- The Right Configuration & Setup – A single misstep in setup can ruin anonymity.
- The Right OPSEC – Even with the perfect device, your behavior can still expose you.
Each of these elements is crucial—fail at one, and you fail at all three.
Anonymity protects your identity from being linked to the device.
A private phone is not necessarily an anonymous one.

🔴 Privacy Phones Options
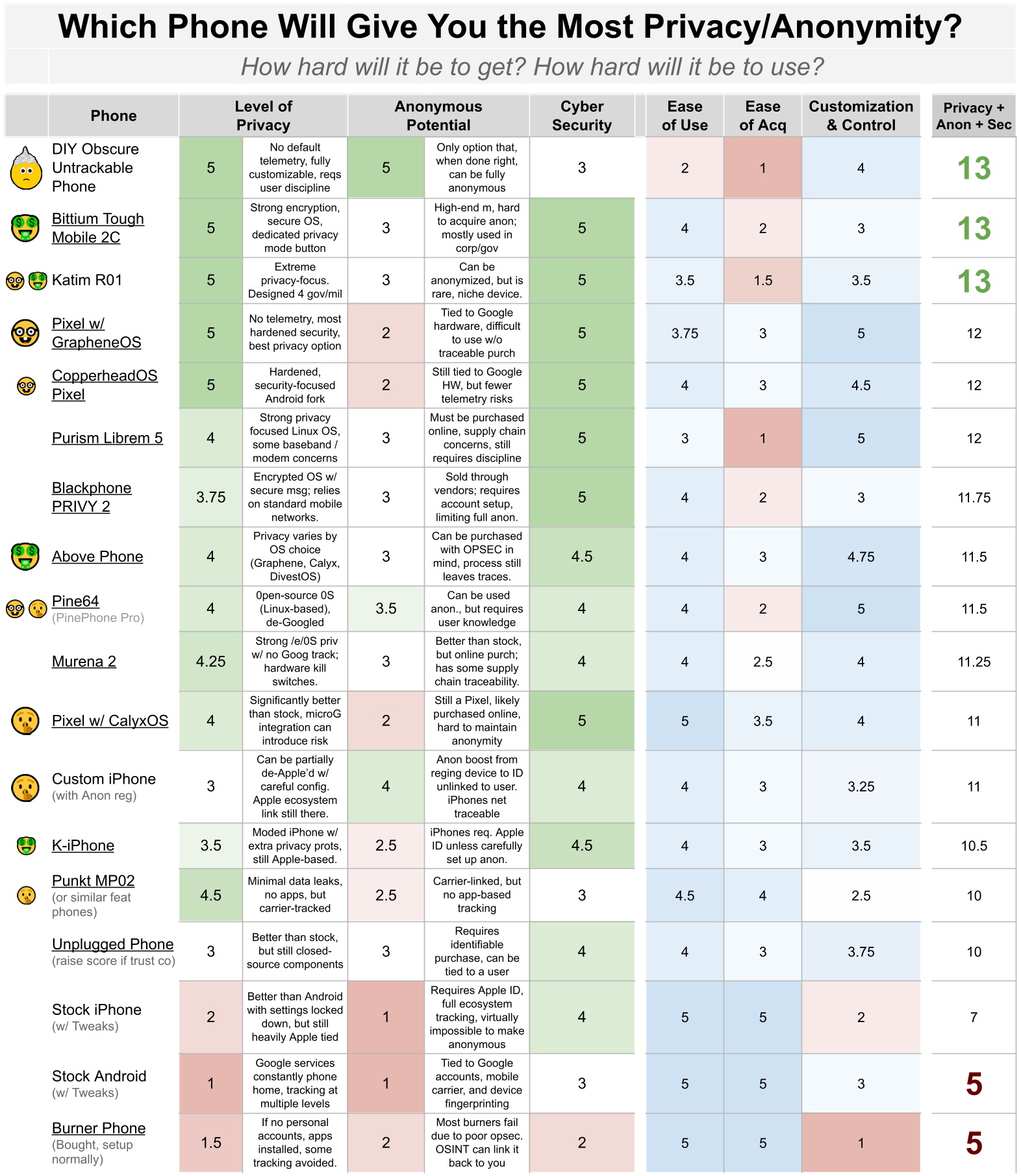
This matrix assesses different phones based on their privacy features, anonymity potential, security, ease of use, and ease of acquisition . Each category is scored from 1 (worst) to 5 (best).Category Explanations:
- Level of Privacy: How well the device prevents data leaks and tracking (telemetry, identifiers, background connections).
- Imagine you have a GrapheneOS Pixel (Privacy Score: 5). It’s great at preventing Google and app-based tracking, but if you bought it with a credit card on Amazon, activated it with your home Wi-Fi, and use it for personal calls, your Anonymity Score drops to 1 or 2.
- Anonymity Potential: How difficult it is to link the phone back to your real identity.
- You could have a cheap prepaid burner phone (Anonymity Score: 5) that you paid for in cash and activated at a random location, but if it’s running stock Android with Google services, it could be leaking data constantly (Privacy Score: 1-2).
- Ease of Use: How practical the device is for daily use without requiring constant technical maintenance and OPSEC.
- Ease of Acquisition: How hard is it to acquire the phone and how much purchasing OPSEC is required?
- Security: Strength against exploits, malware, and surveillance techniques.
- Customization & Control: The ability to modify and harden the device against tracking or security risks.

🔴 Phone Recommendations by User Type
🤓 Tech-Savvy & Want the Best Privacy Protection?
- Best Option: Pixel with GrapheneOS
- Why? Highest security & privacy when configured correctly.
- Trade-offs: Requires flashing GrapheneOS & manual setup.
- Alternative: CopperheadOS Pixel (More security-hardened, but still Google-based).
- For the Linux-savvy: PinePhone Pro (Linux-based OS, full control, but requires advanced setup).
- For extreme security: Katim R01 (Government-level privacy & tamper protection, but rare & hard to buy).
_________________________________
🤑 Have Money But No Time? Want Privacy on Demand?
- Best Option: Bittium Tough Mobile 2C or Above Phone
- Why? Pre-configured for security & privacy—no setup required.
- Trade-offs: Expensive, harder to buy anonymously.
- Alternative: Katim R01 (If you can get one, it offers extreme security).
- For an Apple user: K-iPhone (Modified iPhone with privacy improvements, but still in Apple’s ecosystem).
_________________________________
🤫 On a Budget But Have Time to Tinker?
- Best Option: Pixel with CalyxOS or Custom iPhone (Anon Registration)
- Why? More affordable than other options while offering strong privacy.
- Trade-offs: Still requires setup (flashing CalyxOS or anonymizing an iPhone).
- Alternative: PinePhone Pro (Full Linux control, but steep learning curve).
- For a minimalist option: Punkt MP02 (Basic feature phone with strong privacy, but still SIM-tracked).

🔴 Why Graphene as a Top Choice?
We'll let TheHatedOne explain. He says: "GrapheneOS has a far-reaching number of substantial improvements that altogether make up for the most secure mobile operating system for the end user. "

⚡ Full Guide: Detailed Steps & Technical Walkthrough Below
(For those who want every detail, keep reading.)
Creating an untraceable phone is about blending in and avoiding behaviors that make you stand out. By using everyday tools, like prepaid SIMs and mid-range devices, and following simple privacy habits, you can make it costly and challenging for anyone to track you. Perfect privacy isn’t achievable, but this guide shows how to make it incredibly difficult for adversaries.
🔴 5 Steps to an Untrackable Phone
- Step 1: Preparation (Buying Without a Trail)
- Step 2: Secure the Device (Wipe, Install, Harden)
- Step 3: Anonymous Setup (Accounts, VPN, Activation)
- Step 4: Load Secure Apps (Messaging, Browsing, DNS)
- Step 5: Stay Anonymous in Use (Continuous OPSEC)

Below are the detailed instructions for Building an Untrackable Phone.
[Wire subscribers and ObscureIQ clients]

For the FULL version that includes every detail, visit this link:
How to Set Up a Phone That Can’t Be Traced

🔴 Cheat Sheet for Staying Anonymous
The process centers on a layered approach to anonymity. Think of it as building a fortress—each layer adds another barrier, making it harder for someone to break through. Here’s how it works:
- Separate Your Identity: Use cash and prepaid options. Never link your phone, accounts, or payments to your real identity.
- Choose Privacy-Friendly Tools: Use mid-range phones and prepaid SIMs without personal details. Start with secure apps like Session or Signal for encrypted messaging, and consider adding a privacy-focused operating system, such as GrapheneOS or CalyxOS, for enhanced protection.
- Minimize Your Digital Footprint: Avoid personal networks (home, work) and stick to prepaid mobile data. Public Wi-Fi is risky unless used carefully..
- Disable Tracking Features: Turn off GPS, Bluetooth, and unnecessary permissions. Use privacy-focused browsers like Tor or Brave.
- Keep It Separate: Don’t mix your anonymous phone with personal accounts, devices, or familiar networks.
- Stay Unpredictable: Avoid routines—rotate where you shop, use public Wi-Fi, and keep behaviors unpredictable.
- Refresh Often: Periodically wipe and reset your phone. Tools like Faraday bags can help block signals when not in use.
By following these principles, you’ll build a phone setup that’s tailored for privacy. Whether you’re new to the idea or an experienced privacy advocate, this guide equips you to stay ahead of the game and make your digital life as anonymous as possible. Ready to get started? Let’s dive in:

⭕ Step 1: Preparation
1. Use Cash
- Buy a prepaid SIM card and gift card with cash at large retailers. Select carriers like ⭐ Mint Mobile, ⭐ Tracfone, or Lycamobile, which don’t require IDs. It's best to purchase at a large busy retailer where you never shop. Use cash.
- Obtain an Apple Store or Google Play gift card with cash, depending on your choice of OS. Use a different retailer. If you want to purchase other types of gift cards to enhance privacy of transactions, see this Guide: >> ObscureIQ's Guide to Prepaid Cards.
2. Get a Device
- Buy a used phone with cash (local pawn shops or online marketplaces) or reuse an old one. Ensure no ties to your personal identity.
- Don’t get a current version, but something a couple of years old. It will have less tracking and still do what you need.
- If you want detailed advice, see this Guide: >> ObscureIQ’s How to Buy a Used Phone for Privacy.

⭕ Step 2: Secure the Device
1. Factory Reset the Phone
- Erase all existing data by performing a factory reset.
2. (Optional for Android) Install a Privacy-Focused OS
- Use GrapheneOS or CalyxOS
3. Turn Off Tracking Features
- Disable Bluetooth, GPS, and unnecessary permissions like advertising IDs and analytics, personal assistants, etc..
4. Setup a VPN
- Install a VPN like Mullvad or ProtonVPN. Mullvad is unique because it doesn’t require an email address, allowing you to set up a VPN without compromising privacy.
⭕ Step 3: Set Up Phone Anonymously
Using public Wi-Fi to set up a VPN before activating your anonymous phone is crucial because it prevents any direct connection between your device and a location or network that could identify you. This ensures your phone's setup is as untraceable as possible.
1. Find Public Wi-Fi
- Use Wi-Fi at a library, café, or public space that is not linked to you.
- Choose a location you rarely visit or never plan to return to.
- Do not use your home or work Wi-Fi.
2. Create Private Accounts
- Create Private Email
With VPN active, use a secure, privacy-focused email provider to create an account without requiring personal information. Recommended options:
- ⭐ Proton Mail: Highly secure, offers anonymous sign-ups, and doesn’t require a phone number.
- ⭐ Tutanota: End-to-end encryption with anonymous account creation and optional paid plans for expanded storage.
- Use non-identifiable information (e.g., random usernames) during sign-up. Avoid anything that can be tied back to you. Do not link this email to any existing personal accounts. No email forwarding. That's inconvenient but important.
- Set Up Your Apple or Google Account, Privately
With VPN active, use your new private email and the gift card you purchased to create an account without using your personal information. Recommended options:
- Input a random billing address if prompted.
3. Activate the SIM Card
- Insert the prepaid SIM card into the phone.
- Activate it using the public Wi-Fi and the active VPN.
- Avoid entering any personal information.

⭕ Step 4: Load Secure Apps
1. Get a Private Browser
- Replace the default browser with Tor Browser or Brave or Duck Duck Go for better privacy.
- Do not use Chrome Browser
2. Get Encrypted Messaging
- Install a secure messaging apps like Session or Signal for private, end-to-end encrypted communication.
- Avoid linking these apps to personal accounts or phone numbers.
3. Disable Cloud Services
- Disable cloud backups like Google Drive and iCloud
- If you want secure Cloud services, use something like Proton Drive

⭕ Step 5: Stay Anonymous
Tips for keeping your anonymity when using your phone. Getting it set up right is crucial, but you can do things that compromise that privacy if you are not careful.
Use Prepaid Mobile Data
- Why? SIM cards generate metadata that logs your location and call history, even if you never make a call.
- How to Do It Right:
- Buy prepaid SIM cards with cash—never use your credit card or personal ID.
- Avoid long-term use of a single SIM—swap periodically to break tracking patterns.
- Activate only in a location you don’t frequent—never at home or work.
- Disable VoLTE & Wi-Fi Calling—these create additional tracking vectors.
- If available, consider using anonymous eSIM services like Silent.Link for short-term numbers.
- Mistakes to Avoid
- Registering the SIM in your real name (if required, use a trusted alias).
- Inserting the SIM into your personal phone before your anonymous phone.
- Keeping the same SIM for too long—swap every few months if possible.
Avoid Public Wi-Fi, But if you must, do it right
- Why? Public Wi-Fi networks log device MAC addresses and can fingerprint your phone.
- How to Do It Right:
- Never connect to personal accounts or familiar services on public Wi-Fi.
- Use a VPN or Tor connection every time you go online.
- If using public Wi-Fi, rotate locations and avoid connecting to the same network twice.
- Turn Wi-Fi OFF when not in use - some networks track nearby devices even if you don’t connect.
- Mistakes to Avoid
- Logging into email, banking, or social media over public Wi-Fi.
- Using "Free Airport Wi-Fi" or other highly monitored networks.
- Leaving your Wi-Fi on - some devices still send background signals.
Rotate Locations, Never Use the Phone in a Routine Pattern
- Why? Repeatedly using the same cell towers builds a traceable pattern, even with a burner phone.
- Using the phone at home or work, even once.
- Making calls or checking messages from the same locations over time.
- Using the same café, library, or other "safe" location multiple times.
- How to Do It Right:
- Use different locations for calls, browsing, and SIM activation.
- Travel to random locations before inserting a new SIM or using mobile data.
- If possible, use a Faraday bag when traveling between locations to prevent passive logging.
- Mistakes to Avoid
- Using the phone at home or work, even once.
- Making calls or checking messages from the same locations over time.
- Using the same café, library, or other "safe" location multiple times.
Stay Separate, Never Link the Phone to Your Personal Life
- Why? If your anonymous phone ever connects with your personal devices, it’s game over.
- Charging the phone at home—smart chargers and Tesla stations log device IDs.
- Using the same voice or typing patterns across devices (AI can analyze speech & keystrokes).
- Leaving Bluetooth enabled—this allows tracking even without Wi-Fi.
- How to Do It Right:
- Never connect to the same Wi-Fi as your personal phone or laptop.
- Never use Bluetooth or NFC—keep them permanently disabled.
- Use different email & messaging accounts—don’t reuse any old credentials.
- If possible, keep separate devices for different purposes (e.g., one for calls, one for browsing).
- Mistakes to Avoid
- Charging the phone at home—smart chargers and Tesla stations log device IDs.
- Using the same voice or typing patterns across devices (AI can analyze speech & keystrokes).
- Leaving Bluetooth enabled—this allows tracking even without Wi-Fi.
Refresh Periodically
- Why? Over time, even a well-maintained anonymous phone collects identifiable artifacts.
- Restoring from an old backup - always start fresh.
- How to Do It Right
- Perform a factory reset every 6-12 months to remove lingering data.
- Swap devices entirely if you’ve had it for too long – don’t get too comfortable with one phone.
- If possible, use a different SIM, new accounts, and fresh apps after resetting.
- Clear all metadata and app history before disposing of or repurposing a device
- Mistakes to Avoid
- Keeping a device for too long; eventually, a pattern will emerge.
- Thinking a reset removes everything - carriers and networks still retain metadata.

⭕ Advanced Tricks
1. Faraday Bag
- Use a Faraday bag when the phone is not in use to block RF signals entirely.
2. Secure DNS
3. Use separate devices for different activities
- Use one for calls, another for browsing. Browsing is often the most dangerous activity.
4. Use separate devices for different activities
- Use one for calls, another for browsing. Browsing is often the most dangerous activity.

Disclaimer
The tools and services mentioned in this guide are recommended based on their current reputation and features as of the time of writing. However, privacy-focused technologies, policies, and security practices can change over time. It is essential to independently verify the current status, terms of service, and effectiveness of any recommended tools or services before relying on them for anonymity or security. Always stay informed by consulting official websites, privacy advocate resources, or trusted reviews to ensure these solutions meet your needs and provide the expected level of privacy.

Member discussion